You might have harvested many things upto now but what we are going to harvest today is something bad :)
Requirements:
- A Linux box (I'm using Kali Linux)
- theharvester program (already available in Kali Linux)
OK stop talking and start doing.
Fire up a terminal in your kali box and type this command:
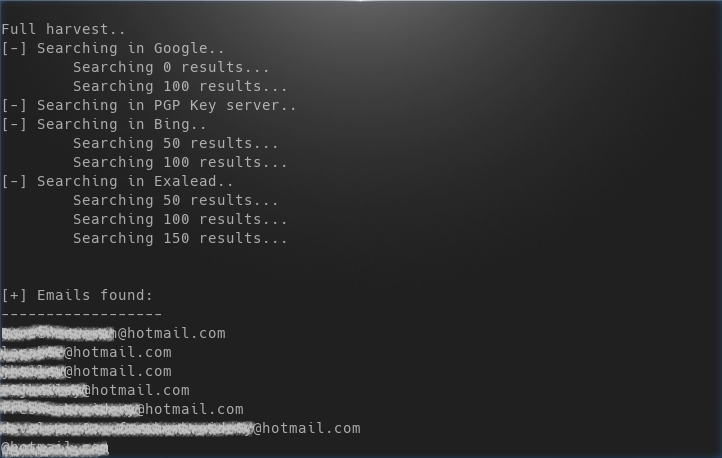
theharvester -d hotmail.com -l 50 -b google
In a small amount of time you'll see your terminal flooded with 200 hotmail.com email address. What does this command mean?
theharvester is the tool name that we are using
-d <domain_name> specifies the domain (or website) who's email addresses we're looking for, in our case it was hotmail.com
-l <number> specifies the number of results that we want in the output, I limited it to 50
-b <source> specifies the source on which to look for email addresses, I specified google as the source
Besides google we can specify any of the follow as source:
google, googleCSE, bing, bingapi, pgp, linkedin, google-profiles, people123, jigsaw, twitter, googleplus, all
Here the last entry all means look in every available source.
Let's say you wanted to look in every available source they you should specify the following command:
theharvester -d hotmail.com -b all
-f is another great flag which can be utilized to save the output in case we want to SPAM them later (just kidding) or for other reasons (I'm thinking positive). -f flag saves the result in html or xml format. Let's do just that:
theharvester -d gmail.com -l 50 -b google -f emailaddresses.html
here -f flag is followed by the location where we want to store the file and the name of file, in our case we stored it in our pwd (present working directory) with the name emailaddresses.html.
Above picture shows an html output generated by harvester.
That's it for this tutorial hope to see you next time!
- Hackers Toolbox
- Hacking Tools Free Download
- Hack Tools
- Hacking Tools Name
- Best Hacking Tools 2020
- Hacker Search Tools
- Pentest Tools For Windows
- Hacking Tools For Pc
- Hacking Apps
- Hack Tools
- Pentest Tools Tcp Port Scanner
- Hacker Tools
- Hacking Tools And Software
- Hackrf Tools
- Hacker Tools Hardware
- Pentest Tools Download
- Github Hacking Tools
- Pentest Tools Alternative
- Nsa Hack Tools Download
- Free Pentest Tools For Windows
- Hacking Tools For Games
- Pentest Tools Download
- Hacking Tools Online
- Underground Hacker Sites
- Hacking Tools Pc
- Hacker Tools Linux
- Hacking Tools Hardware
- Hack Tools For Games
- Hacking App
- Hack And Tools
- Hacker Search Tools
- Hack Tool Apk No Root
- Nsa Hack Tools
- Physical Pentest Tools
- Hacker Tools 2019
- Pentest Tools Linux
- Hacker Techniques Tools And Incident Handling
- Bluetooth Hacking Tools Kali
- Pentest Tools Tcp Port Scanner
- Pentest Tools Download
- Hacks And Tools
- Hacking Tools 2019
- Black Hat Hacker Tools
- Hack Tools For Ubuntu
- Pentest Tools Website Vulnerability
- Blackhat Hacker Tools
- Tools For Hacker
- Hacker Tools For Pc
- Hacker Hardware Tools
- Hack And Tools
- Pentest Tools Website Vulnerability
- Hacker Tools Free
- Hacking Tools For Mac
- Tools Used For Hacking
- Pentest Tools Url Fuzzer
- Pentest Tools Website Vulnerability
- Hacker Tools Hardware
- Hacker Tool Kit
- Hacker Tools List
- Pentest Tools Open Source
- Game Hacking
- Hacking Tools For Windows Free Download
- Tools 4 Hack
- Free Pentest Tools For Windows
- Hacker Tools Github
- Hacking Tools For Windows Free Download
- New Hack Tools
- Black Hat Hacker Tools
- What Are Hacking Tools
- Hack Rom Tools
- Hackrf Tools
- Hacker Techniques Tools And Incident Handling
- Android Hack Tools Github
- Hacker Tools Mac
- How To Hack
- Hacks And Tools
- Hacking Tools
- Hacker Tools For Windows
- Nsa Hack Tools Download
- Hacker Tools
- Pentest Box Tools Download
- Hacking Tools Windows
- Pentest Tools Review
- Pentest Tools Download
- What Is Hacking Tools
- Pentest Tools Website
- Hacking Tools For Games
- Computer Hacker
- Pentest Tools Tcp Port Scanner
- Hackers Toolbox
- Hacking Tools Pc
- Hack And Tools
- Pentest Tools Website
- Pentest Tools List
- Hacker Tools For Windows
- Hack Tools Github
- Hack Tools Mac
- Physical Pentest Tools
- Growth Hacker Tools
- Install Pentest Tools Ubuntu
- Hack Tools Github
- Hacking App
- Hacking Tools
- Easy Hack Tools
- Hacker Tools 2020
- Hacker Tools Free
- Hacking Tools
- Pentest Tools Nmap
- Pentest Tools For Ubuntu
- Pentest Box Tools Download
- Hacking Tools For Beginners
- Usb Pentest Tools
- Hacker Tools For Mac
- Hacking Tools
- Physical Pentest Tools
- Pentest Tools Subdomain
- Hacker Tools For Pc
- Hack Tools Pc
- Hacker Tools For Ios
- Pentest Tools Linux
- Pentest Tools Tcp Port Scanner
- Hack Tools For Windows
- Pentest Tools For Mac
- Hackers Toolbox
- Hacking Tools For Windows 7
- Hacking Tools For Games
- Github Hacking Tools
- Hacker Tools Hardware
- Hacker Techniques Tools And Incident Handling
- Hacking Tools Name
- Hacker Tool Kit
- Underground Hacker Sites



No comments:
Post a Comment